Hello and welcome once again!
Today we are going to be talking about a tool that is used in Kali Linux called Netcat. According to the manual, it is the “TCP/IP Swiss Army Knife,” pretty much stating how useful it is when dealing with those two internet protocols.
In this blog today we will be learning the following about Netcat:
- How it Works
- Listening for Connections
- Sending Messages
- Port Scanning
- Transferring Files
How it Works
nc host port
nc 127.0.0.1 30000In a bash command prompt, we type in either ‘nc’ or ‘netcat’ (they’re the same) as well as the host ip and the port specified. When specifying this, netcat will then open a TCP connection to the port that the user specified on the host itself. Your standard input is then sent to the host and anything coming back from the host is your standard output. So, anything that you type into your command prompt that is your standard input (STDIN) is then sent by Netcat through a TCP connection to the host on the port you specified. Also remember this important point about Netcat: the connection will stay alive until the network side of the connection shuts down.
Listening for Connections on Netcat
Netcat also reads connections as well, acting like a server with a simple command:
nc -l -p 30000The only difference we see with this command is the -l option where it specifies Netcat to ‘listen’ on that port (where -p is the port we specify).
Now that we know these two key concepts about Netcat, let’s try it ourselves! Fire up a machine that has bash, if you have Kali Linux then you will already have Netcat installed, and if you don’t then get it installed! Let’s open two terminals – one for the server side that will be listening for the message and one that is the client-side where it will be sending the message.
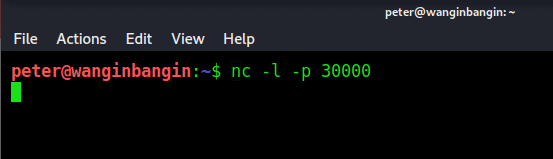
On the server side type in the following:
nc -l -p 30000We are now listening on port 30000 of our local host machine. You should just see a blinking cursor after like in this screenshot:
Sending Messages
Now lets get our client to send the message to our server. Open your other terminal and type the following:
echo "Hello World!" | nc 127.0.0.1 30000Now if you go back to the server terminal you should see the following:
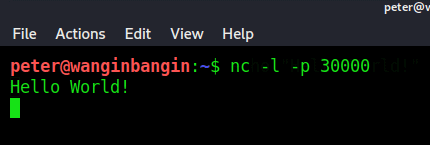
We did it! We just sent our first message through Netcat from a client to a server! Let’s break down the client-side command and how it works:
Remember earlier we said that standard input of the terminal will be sent to the server – this is the reason we use echo “Hello World!” because that is our standard input for Netcat. Then we pipe that command into the Netcat command that specifies the host and port – pretty easy right?
Port Scanning
Netcat also has the ability to perform port scanning. If we look at the manual we can see an option: -z where it implies that it will scan the ports specified by the user:
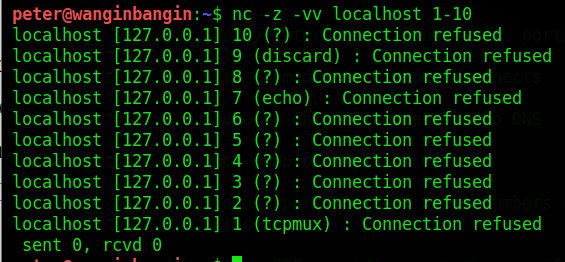
Here we specified the -z command as well as the -vv which tells Netcat to output a more verbose version of the text (show more of whats going on) as well as the host (localhost) and the port range (which in this case are ports 1-10). As a pentester we can find which ports are open and try to exploit them.
Transferring Files
We can also transfer files through Netcat from client to server! We have a file named test.txt which contains the text: “I have been transferred by netcat to this machine. Do not mind me.” We will now have the client send it the server (in this case it will all be done on the same computer and the host is obviously localhost). This may get a little confusing but just go through it slowly and ensure you understand what you are doing step by step:
To get the server to listen on the port we will use the command shown earlier but with a tiny twist:
nc -l -p 30000 > filename.txtRemember, the code above is the server code because we are “listening” on the connection. We see this new text “> filename.txt” this is going to take the standard output that the server outputs into the file that we specified (in this case there was no file named filename.txt so bash will automatically create the file for you and output the text into that file). In bash the “>” operator redirects the output of the command to whatever you specify. Now lets write the client code in the other terminal:
nc 127.0.0.1 30000 < test.txtFor the client, everything stays the same except for the “< test.txt”. If you are a good analyzer, you probably already are guessing what “<” is used for. Yes, it is to redirect the standard input of the command that you are using. Remember earlier we are using the standard input to have the client communicate with the server and now we are redirecting that to input the test.txt file to be sent to the server that is listening. Once you execute that command you can shutdown the server connection (Ctrl+c). The server file is now present on your machine. Go ahead and read the text file and see that the message was transferred to you. Bravo! You just transferred your first file via Netcat!
Conclusion
In this blog, we learned a lot about the different features Netcat offers form listening to connections, transferring files, port scanning, etc. Netcat is an extremely important tool to learn for the OSCP as we will be using it frequently. A tool is best learned by experimenting with it, finding out what tasks it can accomplish for you, as well as its limitations. There are similar tools to Netcat that are out there, but what really matters is understanding the concept behind how it works and how you can use it to your advantage when pentesting.
Thanks for reading today’s blog– I will catch you all next week!
Peter

